Verified Audits
Technology in the form of accounting systems and connectivity have changed the premium
audit environment. A majority of our clients utilize our Verified Audits for the
following benefits:
- Same degree of thoroughness as a physical audit without the site visit
- Cost savings from lack of travel
- Improved Time Service versus Physical Audits; especially in rural and extreme rural locations
- Flexibility of a telephone appointment for insured and/or their accountant versus a traditional physical appointment
- No size or coverage restrictions; multi-billion dollar payrolls handled for Fortune 1000 accounts
- Insured sign-off after telephone conference available by scan if required
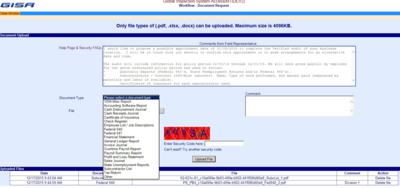 Our GISA - Secure Documents Portal is a professional, secure method for your insureds
to share their sensitive accounting records with our audit staff. The Secure Documents
Portal features:
Our GISA - Secure Documents Portal is a professional, secure method for your insureds
to share their sensitive accounting records with our audit staff. The Secure Documents
Portal features:
- Only certain acceptable file types (e.g. .pdf) can be attached.
Why? These are the file types deemed "acceptable" for security purposes. Other file types may contain malicious code which might go undetected by our anti-virus scans. We are not implying that the user would purposely upload files containing malicious software. Rather, we are accounting for the fact that they may not know if their system and files are compromised with malicious code.
- A security code must be entered for each document to be uploaded.
Why? This is a test to tell computers and humans apart which helps to keep spam robots from automatically uploading files.
- When a user uploads files, they will have access rights to delete them but
will not be able to view them.
Why? We do not control or supply the user's email and we are not their email service provider. Therefore, we do not know if their email and/or email service has been compromised. If their service has been compromised, unknowingly our email to them, which contains the link to our GISA Secure Documents Portal, may have been maliciously sent to other unintended, unauthorized recipients. By only providing any link user with the ability to upload and delete, their documents are secure from outside view.
- The link to the GISA Secure Documents Portal has an expiration date, past which,
the link will not work. The user must contact our field representative, listed on
the email, by telephone, to request another link if this situation arises.
Why? Limiting the operational duration of the link is consistent with the above referenced assumption regarding possible email compromises. In addition, our workflow procedures demand consistent progress milestones which might be degraded with "in perpetuity" links.
- All uploaded documents not required by our customer (typically the user's
insurance carrier) to be included in our final report to them, are deleted from
our GISA Secure Documents Portal servers 30 days after delivery of our report to
our customer.
Why? Any documents uploaded are treated with the utmost confidentiality they deserve. Authorized personnel within our company are required to view and work with these documents within the scope of the performance of our job duty but when that job duty is complete, we believe we should not have access to this information. The 30 day duration before deletion allows our customers and us the time, after their receipt of our report, to efficiently make and answer report inquiries based upon the provided documentation.